Enquire Now
Built for Teams That Can
Not Risk a Breach

From startups to enterprises, our SOC scales to your security needs. We protect finance, healthcare, retail, telecom, and cloud services with continuous threat detection, rapid response, and audit-ready reporting so your business stays compliant and resilient.
-
 Real Estate
Real Estate
-
 Finance & Loans
Finance & Loans
-
 Healthcare
Healthcare
-
 Education
Education
-
 Insurance
Insurance
-
 Hospitality & Travel
Hospitality & Travel
-
 Manufacturing
Manufacturing
-
 Legal Services
Legal Services
-
 Automobile Industry
Automobile Industry
-
 Marketing Agency
Marketing Agency
-
 Consulting Services
Consulting Services
-
 SMEs & MSMEs
SMEs & MSMEs
-
 B2B & D2C
B2B & D2C
-
 Nonprofits
Nonprofits
-
 Fitness & Wellness
Fitness & Wellness
What Makes Our Security Operations Center (SOC) Different from Traditional Security Tools
We combine real-time detection, threat intelligence, automated response, and compliance automation into a single SOC ecosystem. Designed for rapid containment and reduced risk, our service gives you full visibility, faster investigation, and measurable security outcomes.
- 24/7 Threat Monitoring
- SIEM Management & Log Analysis
- Endpoint Detection & Response (EDR)
- Threat Intelligence Feed
-
Incident Response & Forensics
-
Vulnerability Scanning & Management
-
Compliance Monitoring & Reporting
-
Security Orchestration & Automation (SOAR)
-
User & Entity Behavior Analytics (UEBA)
- Cloud & Container Security Monitoring
-
Managed Penetration Testing & Red Teaming
- SOC as a Service (MSSP-ready)
Continuous surveillance across your entire digital environment
Our SOC monitors logs, endpoints, cloud, and networks 24/7 to detect anomalies, intrusions, and data breaches in real time. Suspicious activity is escalated immediately, ensuring no threat goes unnoticed. This proactive vigilance minimizes dwell time and reduces risk.

- Visibility
- Vigilance
- Protection
- Proactivity
- Continuity
Centralized event collection and correlation
We manage and optimize your SIEM platform, turning raw logs into actionable intelligence. Correlation rules highlight hidden attack patterns, while analyst tuning keeps alerts accurate and meaningful. Forensics-ready trails simplify investigations and audits.
- Correlation
- Context
- Precision
- Insights
- Forensics
Detect and contain endpoint threats instantly
Our SOC uses advanced EDR tools to identify malware, ransomware, and fileless attacks at the endpoint level. Compromised devices are isolated within minutes, preventing lateral spread. This ensures faster recovery and stronger endpoint resilience.
- Detection
- Containment
- Speed
- Security
- Control
Real-time context to prioritize evolving threats
We enrich alerts with global and sector-specific threat intelligence. By mapping IOCs and TTPs to your environment, our SOC prioritizes what truly matters. Actionable intelligence helps focus defenses on the most relevant risks.
- Context
- Relevance
- Proactivity
- Prioritization
- Awareness
Fast, structured response when attacks occur
When incidents happen, our SOC springs into action with playbooks, containment measures, and forensic analysis. We trace the root cause, preserve evidence, and guide you with remediation steps to reduce downtime and improve resilience.
- Response
- Recovery
- Forensics
- Control
- Assurance
Continuous exposure management and risk reduction
Our SOC performs regular scans to detect vulnerabilities, misconfigurations, and patch gaps. Risks are prioritized by severity and business impact, feeding directly into remediation workflows. This proactive approach reduces the window of exposure.
- Scanning
- Prioritization
- Remediation
- Risk-Reduction
- Prevention
Automate repetitive tasks, accelerate response
Our SOC integrates SOAR platforms to automate enrichment, response actions, and ticketing. Playbooks orchestrate tools across your stack, cutting response time from hours to minutes. Analysts focus on advanced investigations while automation handles routine steps.
- Automation
- Speed
- Coordination
- Efficiency
- Scalability
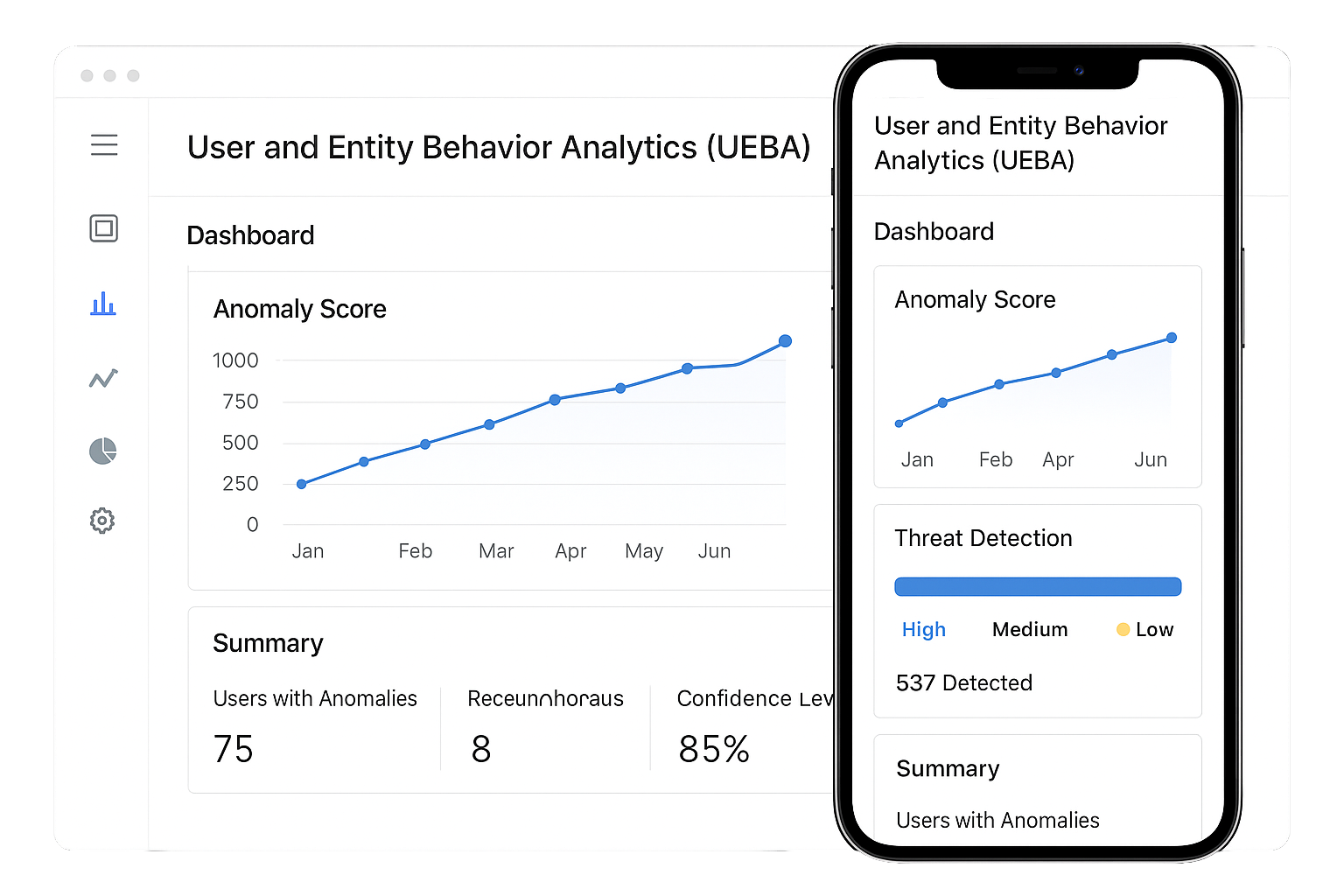
Spot anomalies and insider threats with behavior analysis
UEBA models normal user and device behavior to detect anomalies like privilege misuse, unusual logins, or data leaks. By correlating deviations with threat intelligence, our SOC identifies insider risks and compromised accounts early.
- Behavior
- Anomalies
- Detection
- Security
- Intelligence
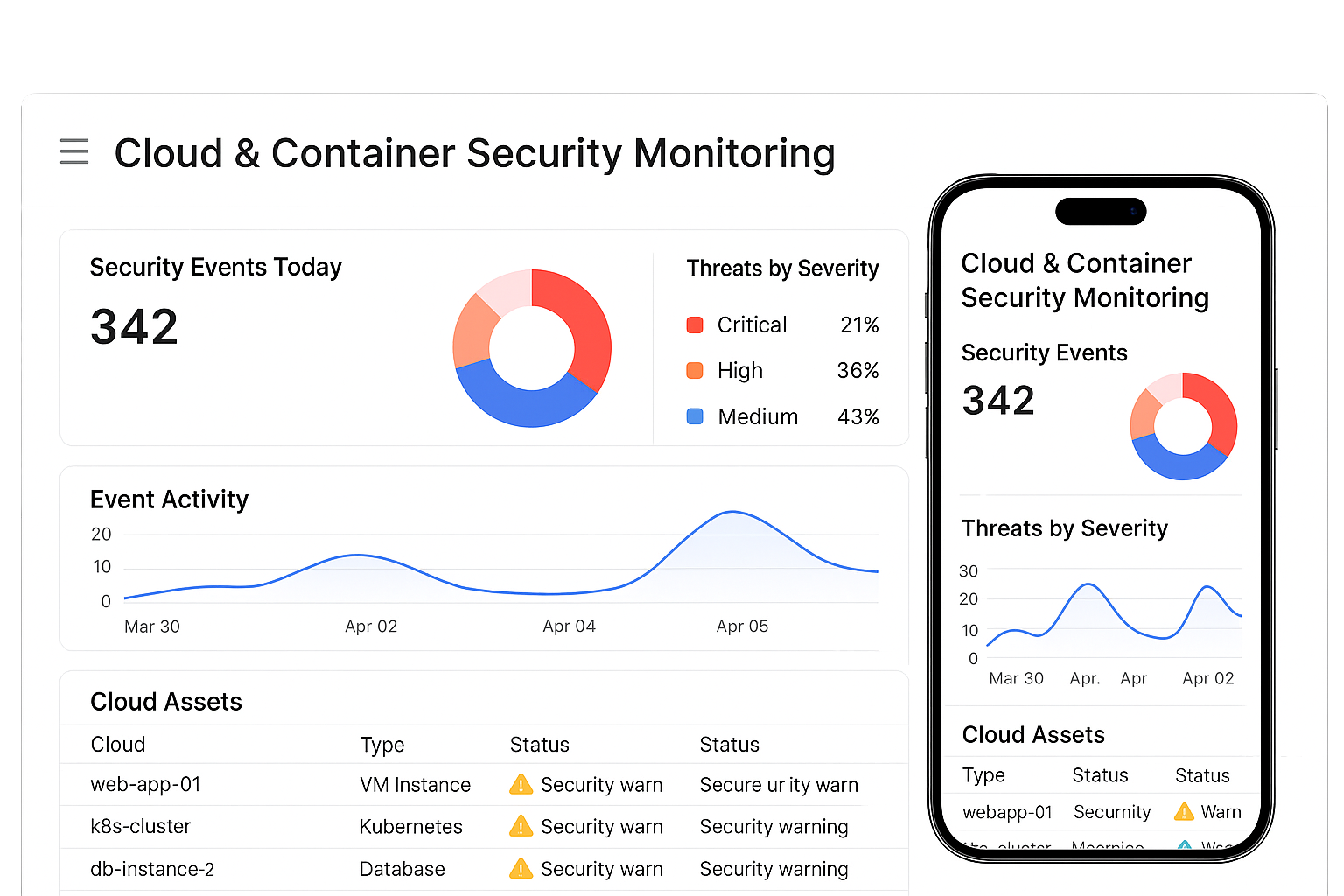
Security visibility across cloud and modern workloads
Our SOC secures hybrid, cloud-native, and containerized environments. We detect misconfigurations, suspicious API activity, and cloud lateral movement. Automated guardrails protect against privilege abuse and data exposure.
- Cloud
- Protection
- Visibility
- Resilience
- Automation
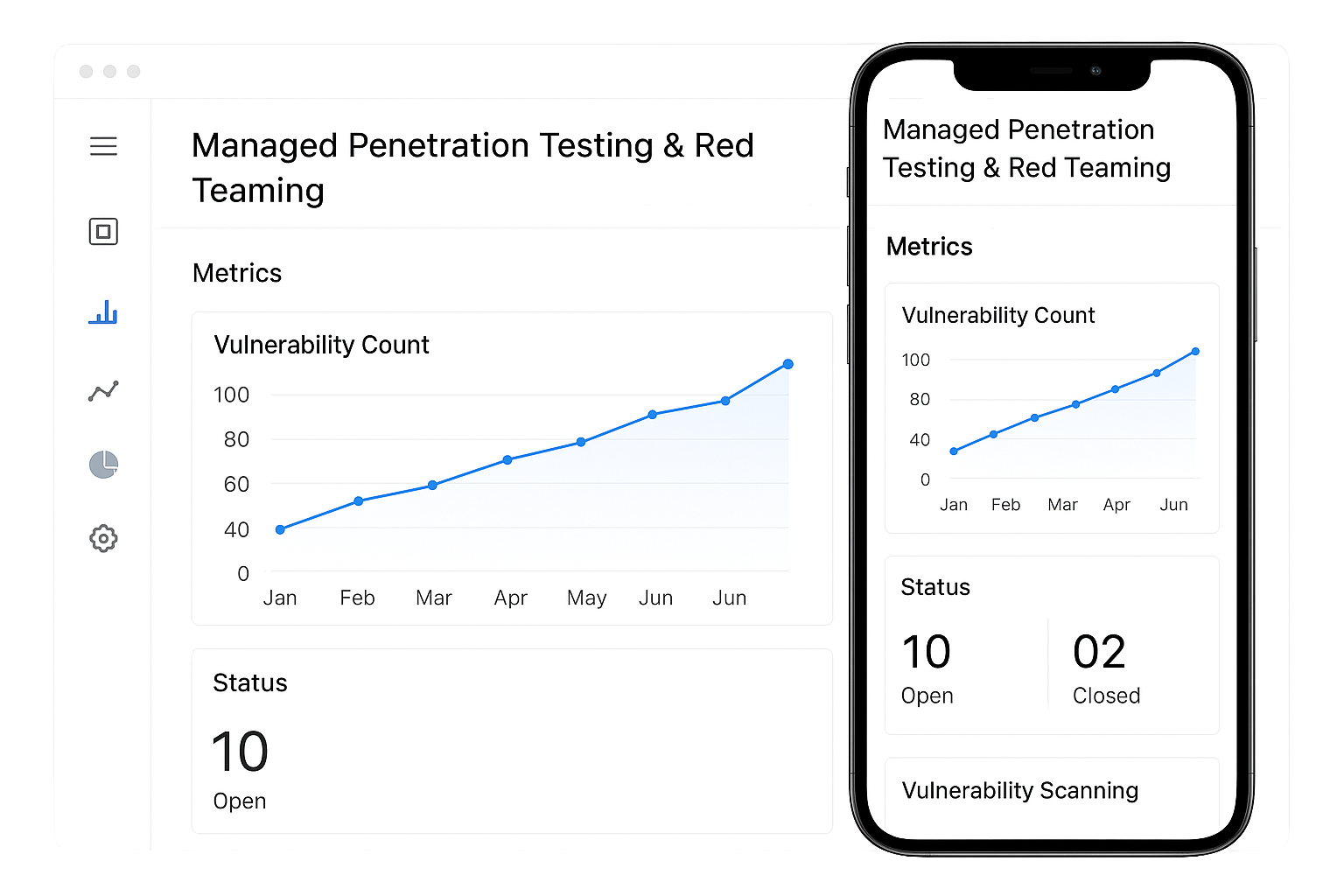
Test defenses with simulated real-world attacks
Our SOC offers continuous pen testing and red team exercises to uncover vulnerabilities attackers might exploit. Findings feed back into SOC tuning and defense hardening, ensuring your organization evolves ahead of adversaries.
- Simulation
- Testing
- Improvement
- Validation
- Hardening
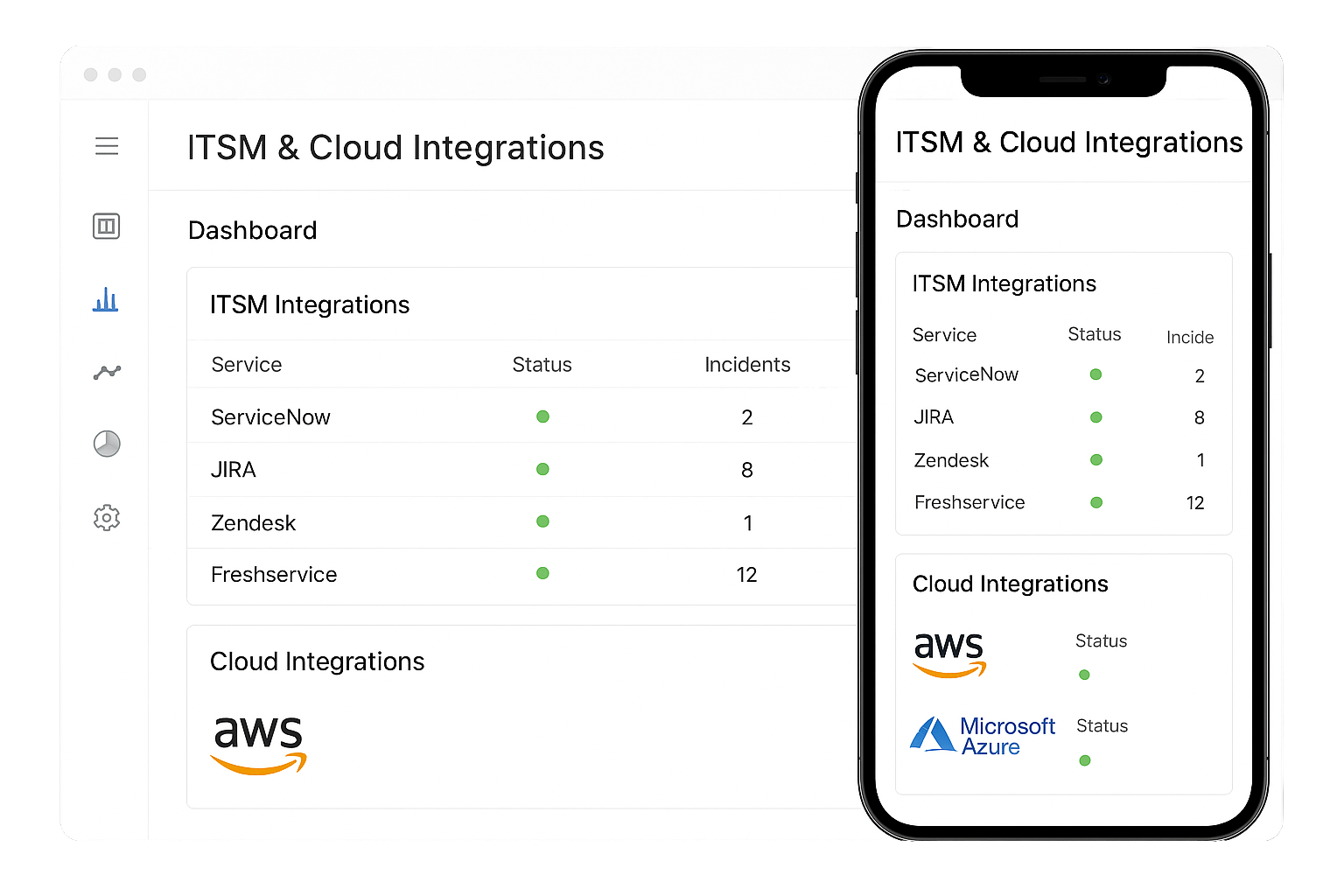
Fully managed SOC with flexible options
Instead of building a costly in-house SOC, outsource to our managed service. Choose co-managed or fully outsourced models. With SLAs, 24/7 analysts, and scalable pricing, SOC-as-a-Service delivers enterprise-grade protection without enterprise overhead.
- Managed
- Flexible
- Scalable
- Affordable
- Reliable

SOC Myths vs Reality: Breaking Common Misconceptions About Security Operations Centers

Many businesses assume SOC services are too expensive, too complex, or only needed by large enterprises. In reality, modern outsourced SOCs are scalable, affordable, and deliver enterprise-grade security for organizations of any size.
My Business Need NOC?
SOC Myths vs Reality:

“Discover the truth about SOC services and learn how modern security operations deliver advanced, cost-effective protection for every business.”
Myth
SOC is only for big corporations
Reality
SOC solutions are modular and scalable, making them perfect for SMBs too.
Outsourced SOC is too costly.
Outsourced SOC reduces staffing, tooling, and infra costs by up to 60%.
In-house SOC gives more security control.
Outsourced SOC delivers broader visibility, 24/7 coverage, and expert response teams.
SOC just means monitoring logs
A true SOC handles monitoring, threat hunting, forensics, incident response, and compliance.
Automation will replace SOC analysts.
SOC automation handles repetitive alerts, freeing analysts to focus on strategic defense.
SOC setup takes years to implement.
Modern SOCs can be deployed in weeks with MSSP-ready models.
In-House SOC vs Outsourced SOC (comparison table)

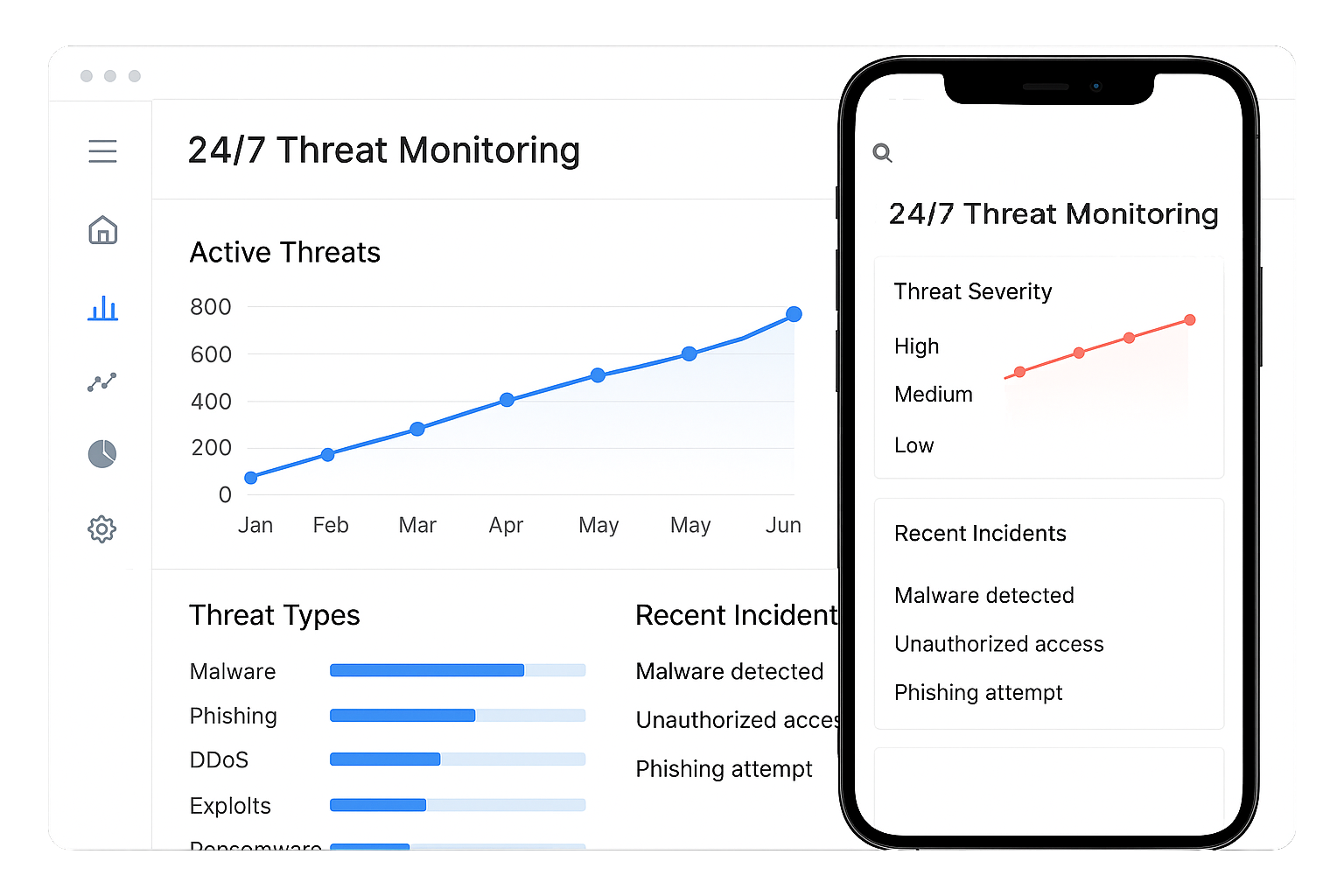
24/7 Threat Monitoring

Our SOC monitors logs, network traffic, endpoints, cloud workloads, and user activity around the clock. We detect signs of compromise, suspicious lateral movement, and data exfiltration in real time. Alerts are triaged by security analysts and enriched with context so only actionable incidents are escalated. Continuous monitoring reduces dwell time and limits blast radius. This is how we turn noisy telemetry into clear security decisions.
24/7 Threat Monitoring

Our SOC monitors logs, network traffic, endpoints, cloud workloads, and user activity around the clock. We detect signs of compromise, suspicious lateral movement, and data exfiltration in real time. Alerts are triaged by security analysts and enriched with context so only actionable incidents are escalated. Continuous monitoring reduces dwell time and limits blast radius. This is how we turn noisy telemetry into clear security decisions.

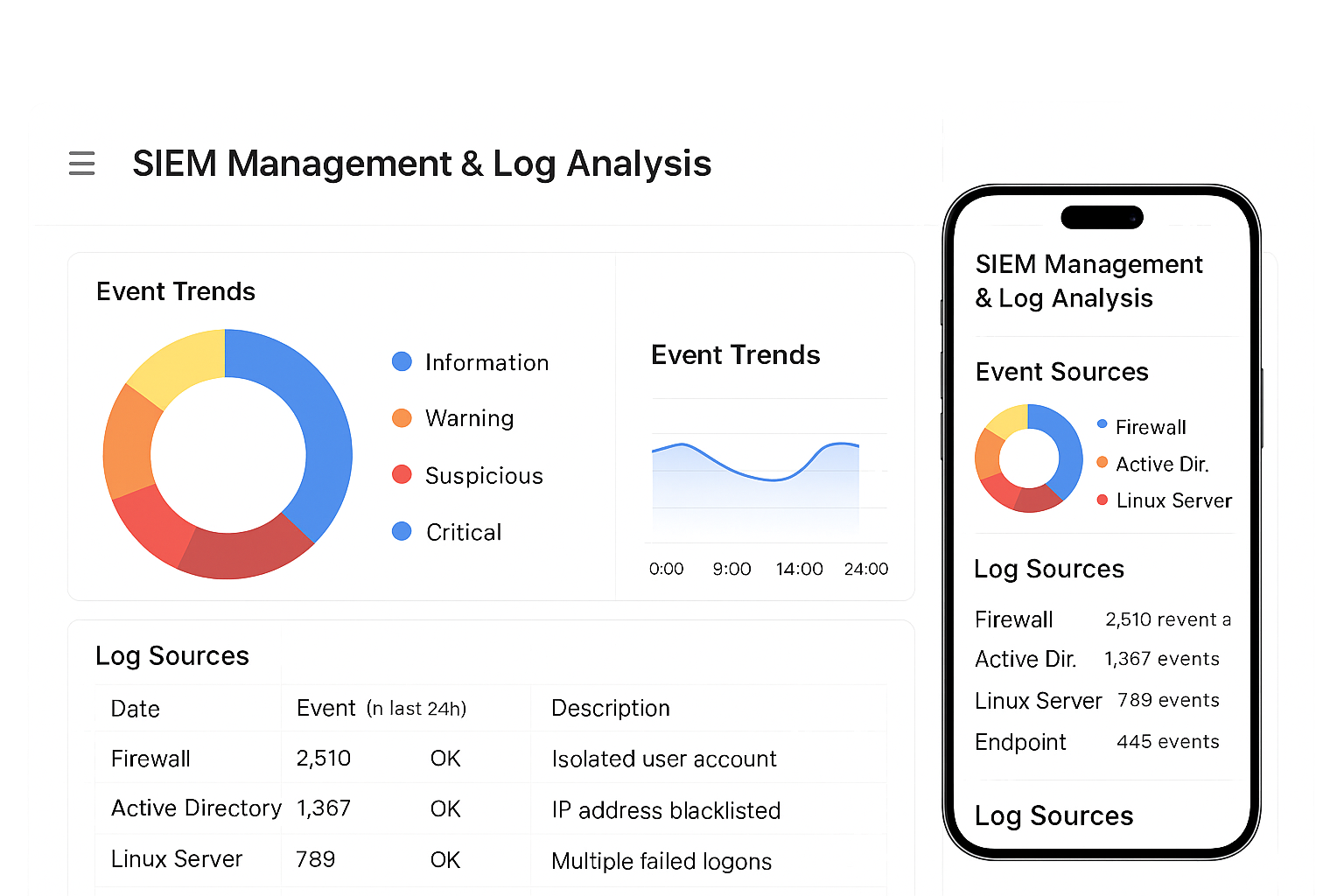
SIEM Management & Log Analysis

We manage your SIEM, tune detection rules, and correlate events across sources to find complex attacks. Raw logs become searchable intelligence, and alerts come with context, priority, and suggested playbooks. Regular tuning minimizes false positives and keeps detection precision high. SIEM as a managed service lowers operational overhead and improves threat visibility. You get forensic trails ready for investigations and audits.
Endpoint Detection & Response (EDR)

EDR agents provide deep visibility into processes, files, and connections on endpoints. Our SOC detects suspicious behaviors, isolates compromised hosts, and executes containment playbooks in minutes. We combine telemetry with threat intelligence to stop ransomware, fileless attacks, and advanced malware. EDR plus analyst validation ensures rapid remediation and reduces spread across the network.
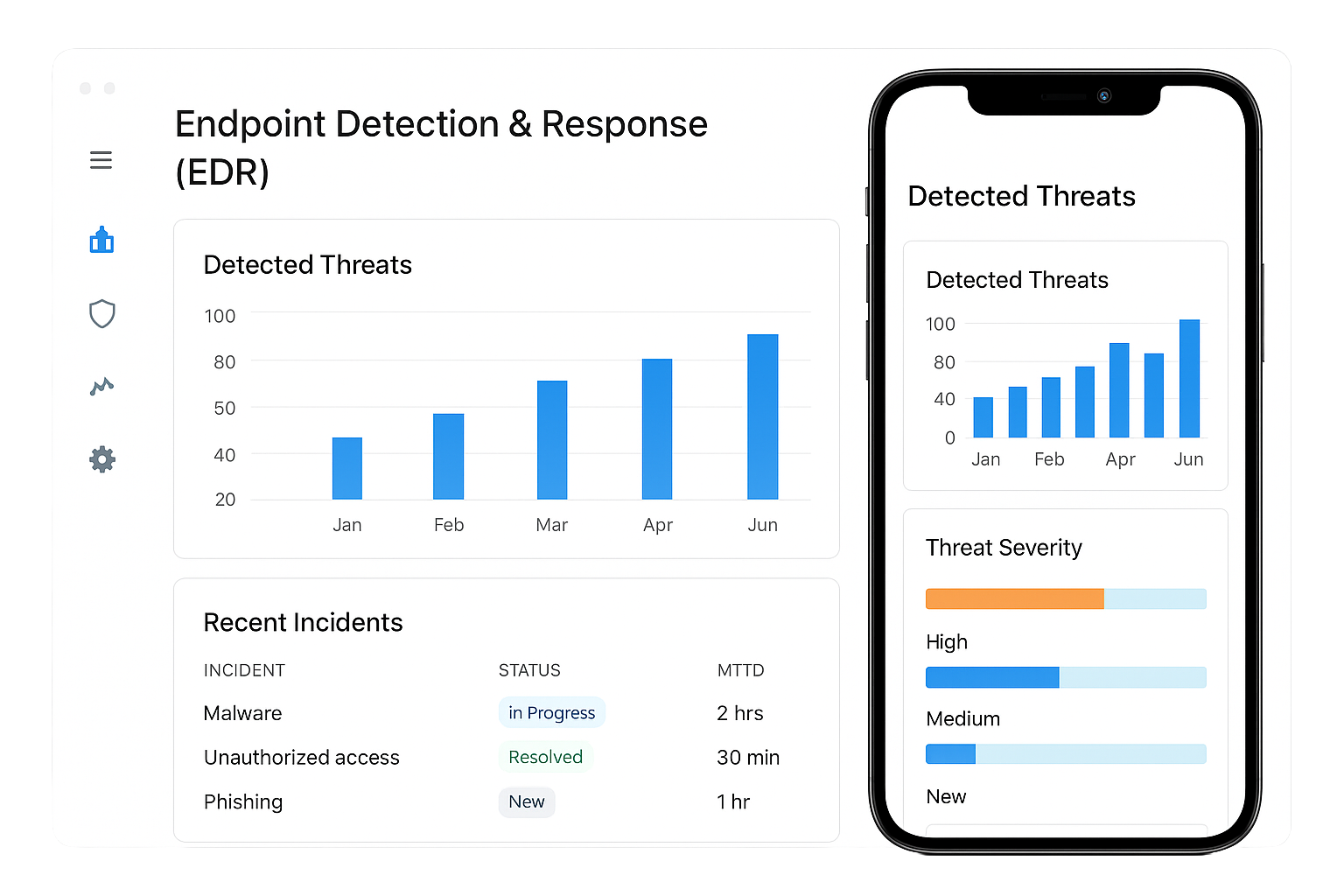
Endpoint Detection & Response (EDR)

EDR agents provide deep visibility into processes, files, and connections on endpoints. Our SOC detects suspicious behaviors, isolates compromised hosts, and executes containment playbooks in minutes. We combine telemetry with threat intelligence to stop ransomware, fileless attacks, and advanced malware. EDR plus analyst validation ensures rapid remediation and reduces spread across the network.

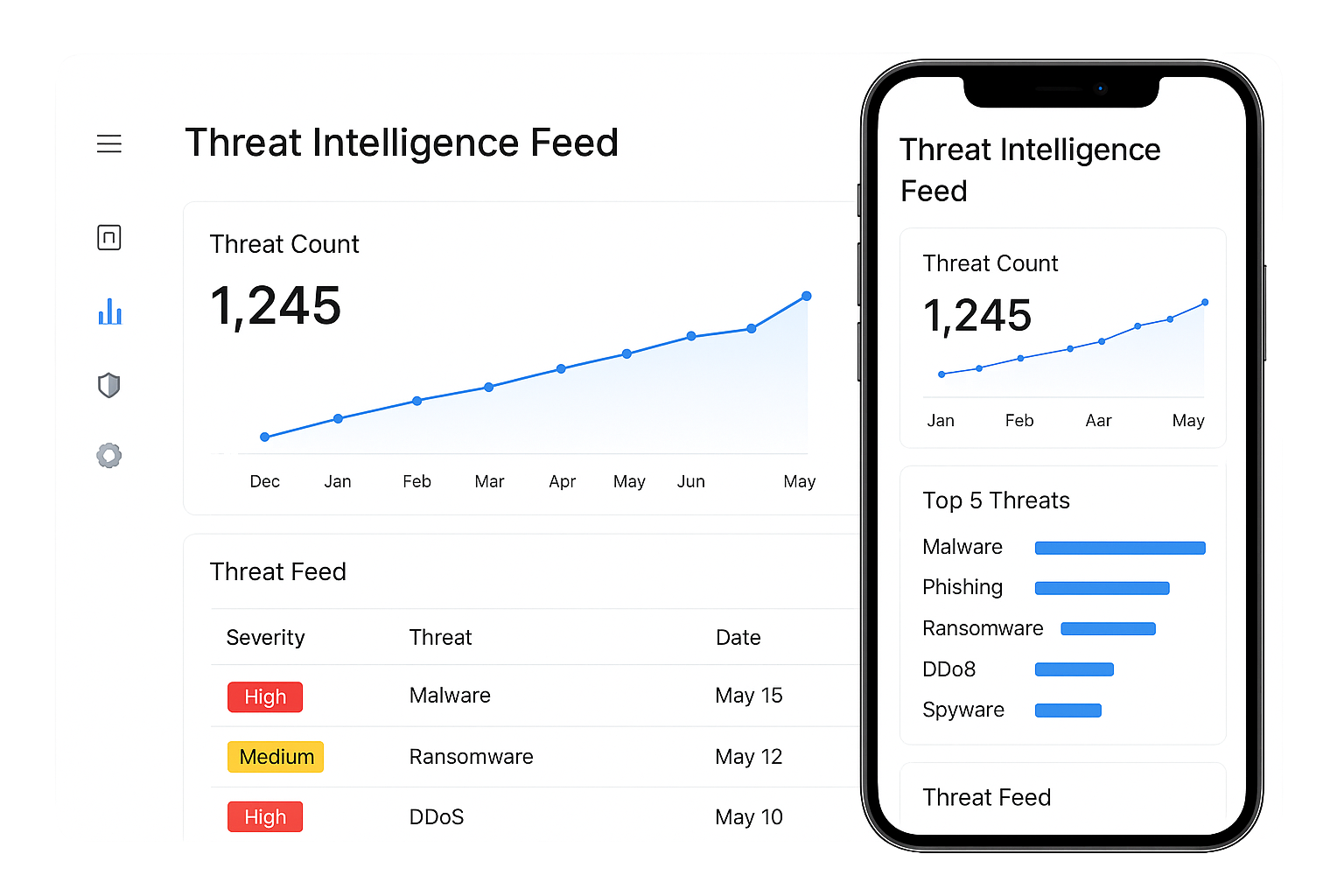
Threat Intelligence Feed

We ingest curated threat intelligence feeds and map IOC indicators to your environment. That means we surface relevant indicators, attacker infrastructure, and emerging TTPs affecting your sector. Analysts use this context to prioritize alerts and enrich incidents with attribution when possible. Actionable intelligence cuts investigation time and guides tailored defenses.


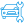
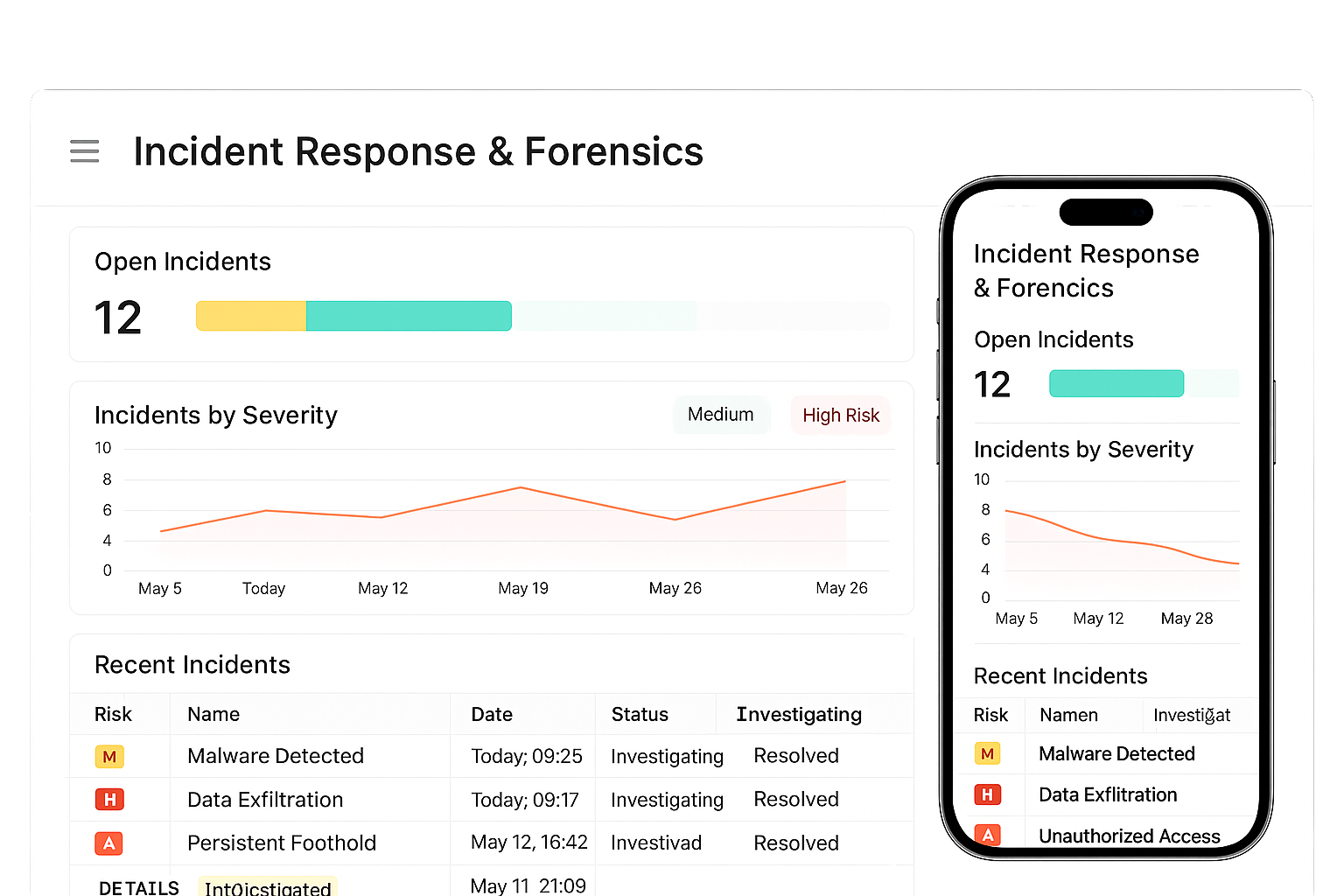
Incident Response & Forensics

Our SOC provides incident playbooks, containment steps, and forensic analysis when incidents occur. We perform root cause investigations, preserve evidence, and produce post-incident reports with remediation plans. If needed, we coordinate with on-site teams or external responders. This reduces recovery time and gives you a clear path to resume normal operations.
Incident Response & Forensics

Our SOC provides incident playbooks, containment steps, and forensic analysis when incidents occur. We perform root cause investigations, preserve evidence, and produce post-incident reports with remediation plans. If needed, we coordinate with on-site teams or external responders. This reduces recovery time and gives you a clear path to resume normal operations.

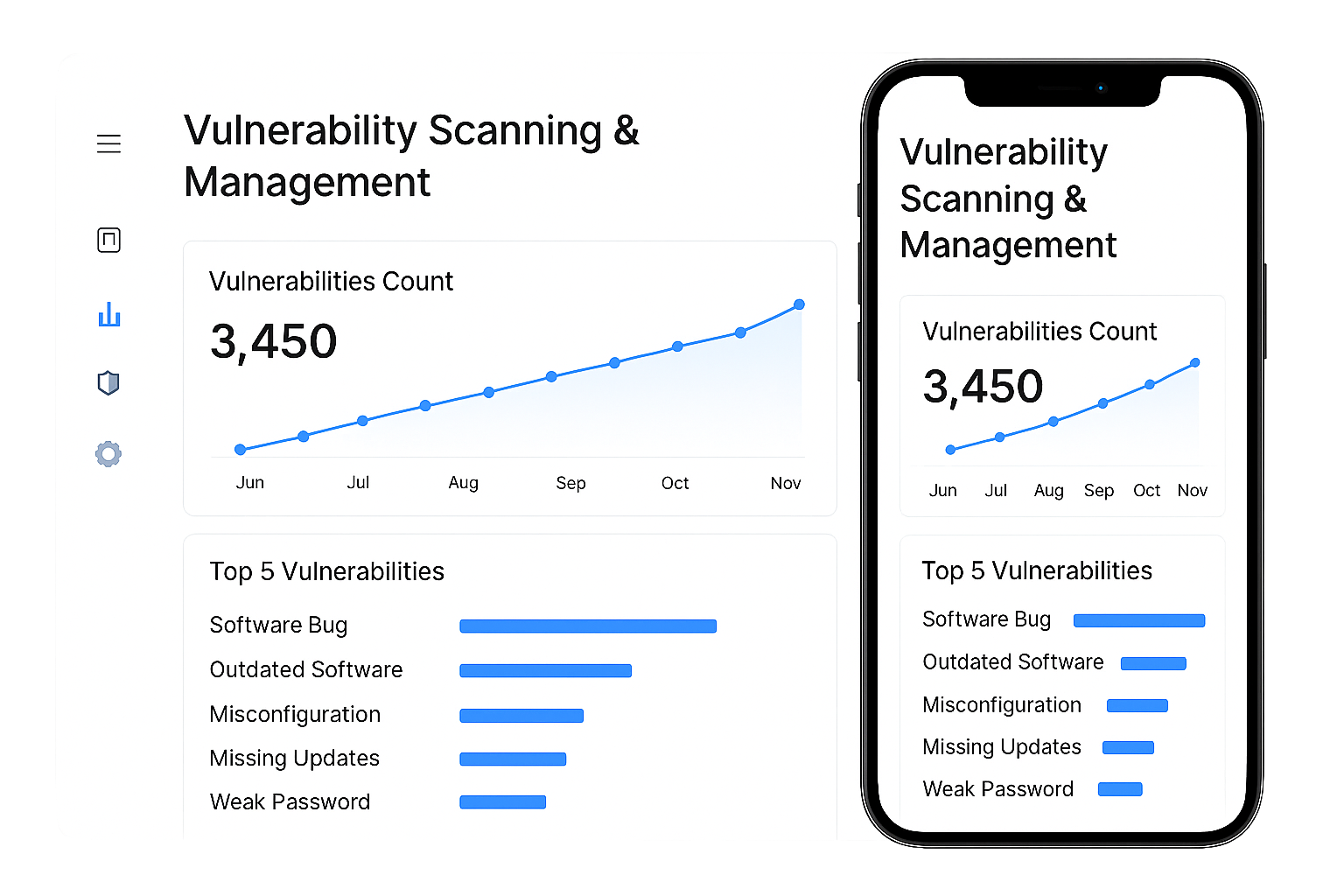
Vulnerability Scanning & Management

We run scheduled and on-demand scans to find missing patches, misconfigurations, and critical exposures. Vulnerabilities are prioritized using risk scoring and business impact, then fed into remediation workflows. Tracking and reporting help you close gaps faster and prove progress to auditors. Proactive vulnerability management lowers the chance of successful attacks.

Compliance Monitoring & Reporting

Our SOC automates compliance controls, collects required logs, and generates ready-to-share reports. We map controls to requirements and keep an audit trail of detections, incidents, and remediations. That reduces audit effort and demonstrates regulatory posture to stakeholders. Compliance monitoring also highlights risky drift before it becomes a liability.
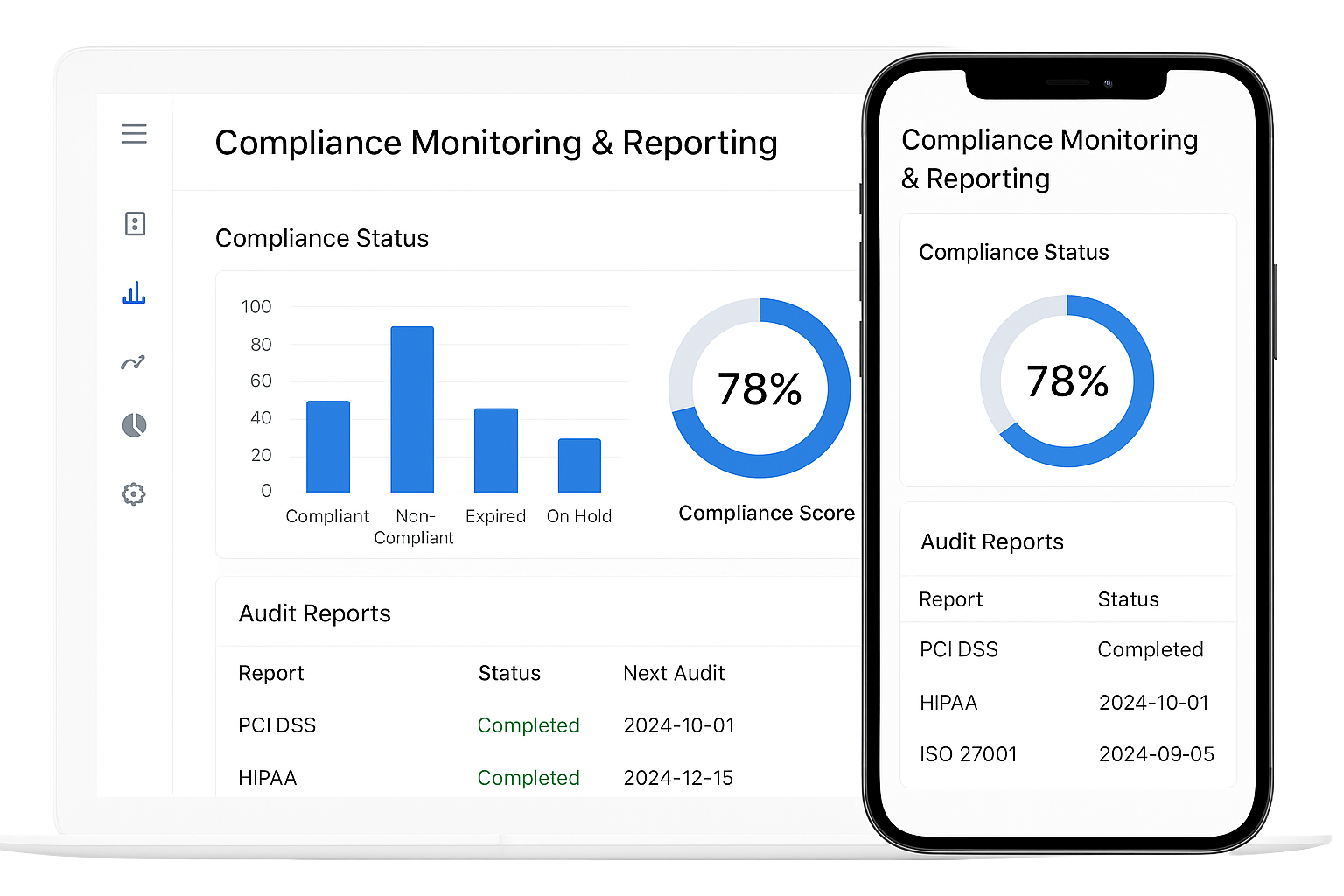
Compliance Monitoring & Reporting

Our SOC automates compliance controls, collects required logs, and generates ready-to-share reports. We map controls to requirements and keep an audit trail of detections, incidents, and remediations. That reduces audit effort and demonstrates regulatory posture to stakeholders. Compliance monitoring also highlights risky drift before it becomes a liability.

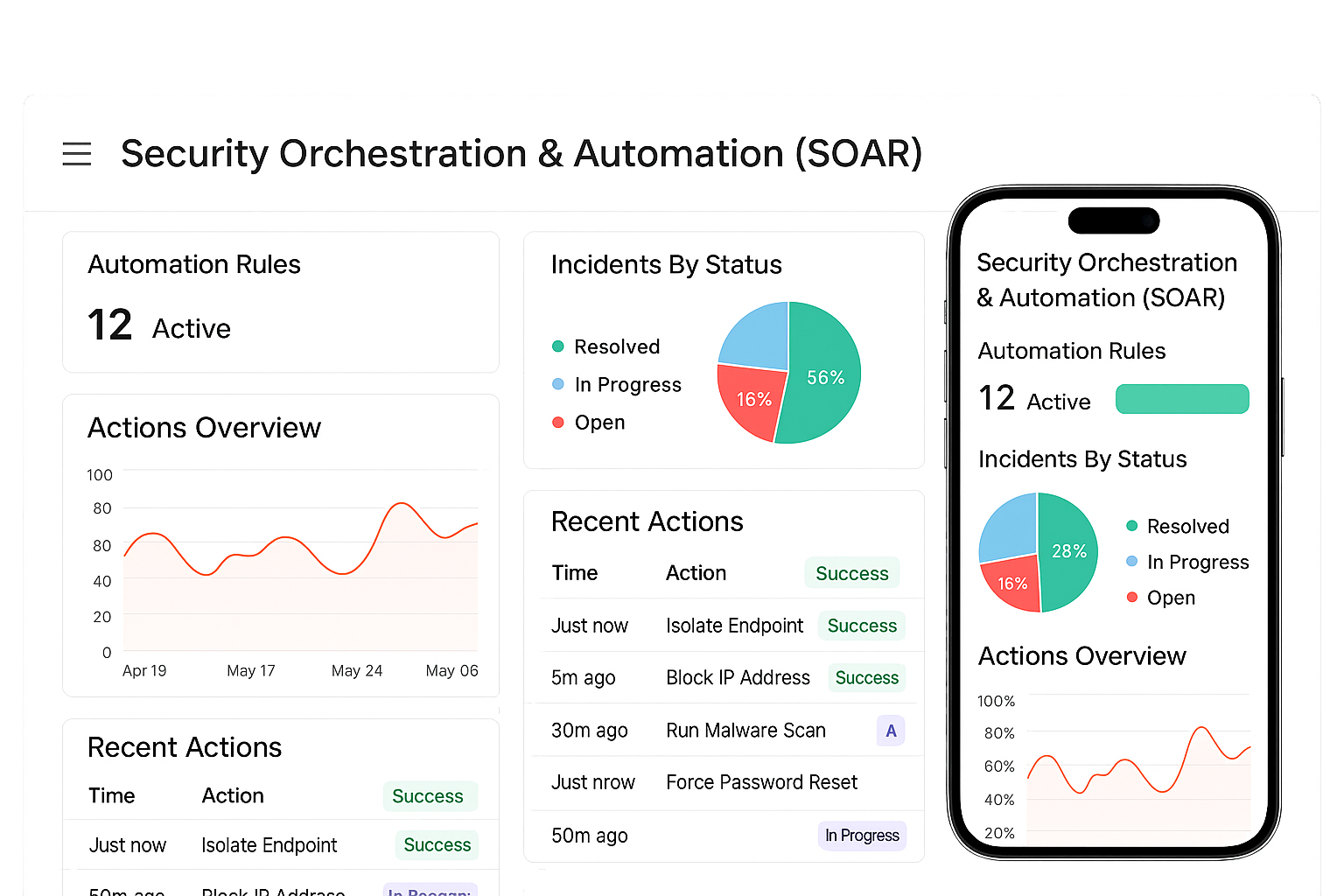
Security Orchestration & Automation (SOAR)

SOAR automates repetitive tasks like enrichment, containment, and ticket creation while letting analysts approve critical steps. Automation reduces human error and speeds containment for common threats. Our playbooks integrate EDR, firewalls, SIEM, and ITSM tools to run coordinated responses. This means faster recoveries and more consistent security operations.


User & Entity Behavior Analytics (UEBA)

Detect insider threats and account compromise using behavior baselines UEBA models normal user and device behavior, then flags deviations like privilege misuse, unusual access times, or data transfers. Combining UEBA with threat intel reveals stealthy attacks that signature tools miss. UEBA helps detect compromised credentials, rogue insiders, and lateral movement early. That gives you a deeper layer of detection beyond static rules.
User & Entity Behavior Analytics (UEBA)

Detect insider threats and account compromise using behavior baselines UEBA models normal user and device behavior, then flags deviations like privilege misuse, unusual access times, or data transfers. Combining UEBA with threat intel reveals stealthy attacks that signature tools miss. UEBA helps detect compromised credentials, rogue insiders, and lateral movement early. That gives you a deeper layer of detection beyond static rules.

Cloud & Container Security Monitoring

Secure workloads across public cloud and container platforms We monitor cloud accounts, workloads, containers, and orchestration layers for misconfigurations, suspicious API calls, and lateral cloud threats. The SOC correlates cloud telemetry with network and endpoint logs for full-stack visibility. Automated checks and guardrails help prevent data leaks and privilege abuse. Cloud security monitoring protects modern apps and hybrid environments alike.


Managed Penetration Testing & Red Teaming

Real-world attack simulations to harden defenses Regular pen tests and red team exercises expose gaps attackers would exploit. We run scoped assessments and deliver prioritized findings plus fixes. Red team engagements simulate targeted adversaries to test detection and response capabilities. Results feed into SOC tuning and training so your defenses actually improve over time.
Managed Penetration Testing & Red Teaming

Real-world attack simulations to harden defenses Regular pen tests and red team exercises expose gaps attackers would exploit. We run scoped assessments and deliver prioritized findings plus fixes. Red team engagements simulate targeted adversaries to test detection and response capabilities. Results feed into SOC tuning and training so your defenses actually improve over time.

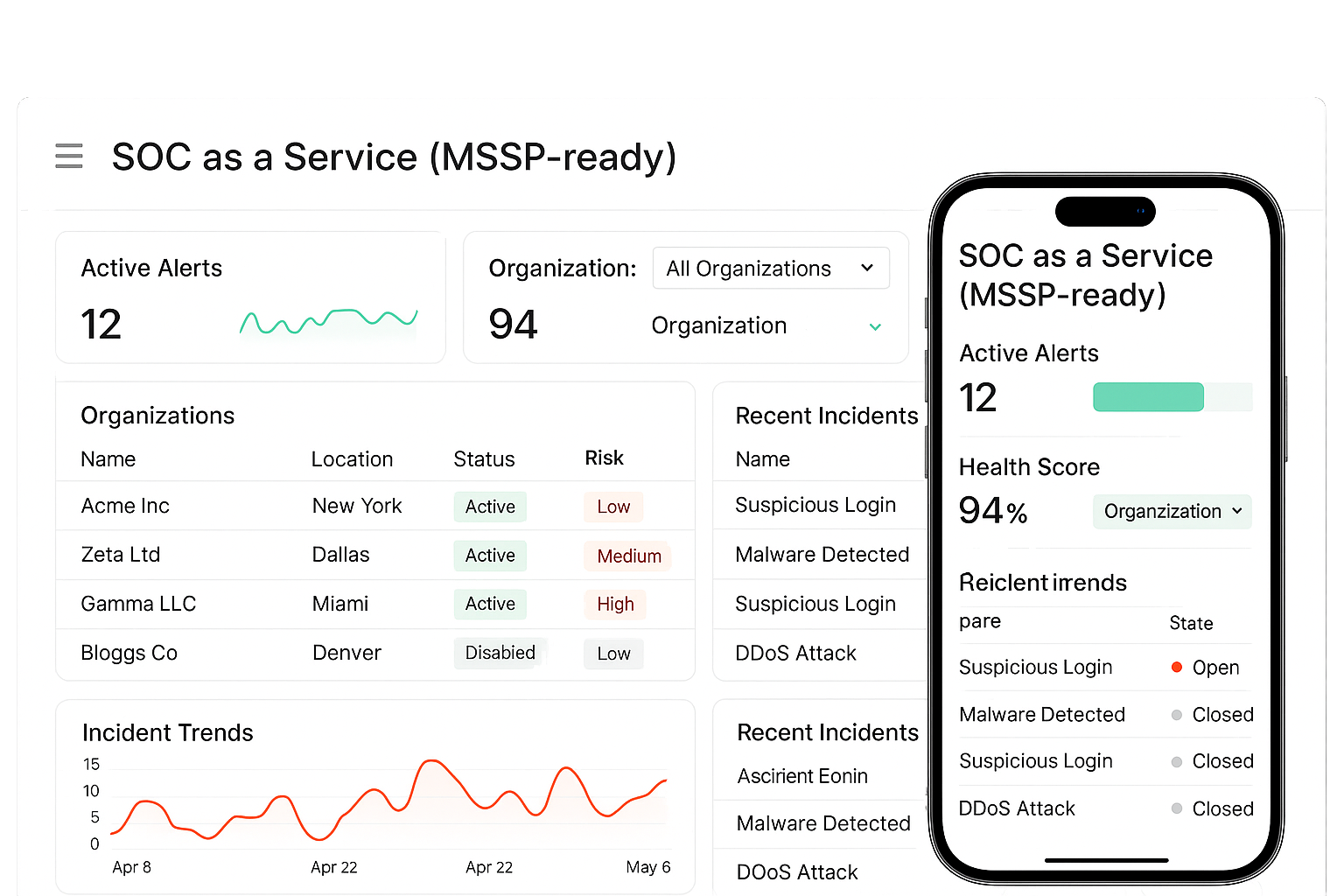
SOC as a Service (MSSP-ready)

Fully managed SOC with flexible engagement models Get a staffed SOC without building one. We offer monitored services, co-managed models, or fully outsourced SOC with SLAs. Services include analyst shifts, threat hunting, incident handling, and reporting. Flexible pricing and onboarding mean you pay for the level of coverage you need. SOC as a Service scales with your risk profile and maturity.
Upgrade Your Cybersecurity: Quisitive
SOC vs The Rest
We are Not Saying Quisitive s Magic But People Think It Is
Got Doubts? Let's Smash 'Em Together
Think of it as your cybersecurity command center, where expert analysts and advanced tools work 24x7 to protect your networks, systems, endpoints, and data from attacks like malware, ransomware, phishing, insider threats, and zero-day exploits.
A SOC uses technologies such as SIEM (Security Information and Event Management), EDR (Endpoint Detection and Response), log analysis, and threat intelligence platforms to identify suspicious activity in real time — then initiates immediate investigation and remediation.
In short:
🔹 SOC = Proactive Cyber Threat Hunting
🔹 SOC = Rapid Incident Response
🔹 SOC = Compliance & Data Protection
Whether built in-house or outsourced as a managed service, a SOC is essential for any business serious about defending against modern cyber threats.
This includes real-time analysis of security alerts, incident triage, forensic investigations, breach containment, and post-event reporting — all handled by certified security analysts using enterprise-grade tools like SIEM, SOAR, and EDR.
Ideal for organizations that lack in-house cybersecurity expertise or want to strengthen their defenses without investing in expensive tools and staffing, SOC as a Service offers:
Around-the-clock protection
Faster mean time to detect (MTTD) and respond (MTTR)
Regulatory compliance support (GDPR, HIPAA, PCI-DSS, etc.)
Scalable coverage for growing IT environments
It’s like having a full-fledged cybersecurity war room — without building one yourself.
24x7 Threat Monitoring: Detect malicious activity at any time, even outside business hours.
Faster Breach Response: Reduce damage and downtime with rapid incident containment and recovery.
Advanced Threat Intelligence: Stay ahead of emerging threats using global threat feeds and behavioral analytics.
Regulatory Compliance: Meet standards like ISO 27001, NIST, GDPR, and HIPAA with audit-ready logs and reports.
Reduced Risk of Data Loss: Prevent ransomware, data exfiltration, and unauthorized access.
Expert Security Team Access: Leverage certified CISSP, CEH, and CISM professionals without hiring them directly.
With SOC as a Service, you gain a powerful defense layer that protects your brand reputation, customer trust, and digital assets.
Banks, fintech, and insurance firms (handling financial data)
Healthcare providers (protecting patient records under HIPAA)
E-commerce & SaaS companies (securing customer databases)
Government & educational institutions
MSPs offering cybersecurity to clients
Enterprises with hybrid or cloud-first strategies
If your business stores, processes, or transmits sensitive information — or has suffered near-misses from phishing or malware, basically for those who can't afford downtime — then a managed SOC service is not just beneficial… It's essential.
Cyberattacks don’t wait. Neither should you.
SOC (Security Operations Center) focuses on cybersecurity. It continuously monitors for threats like malware, ransomware, phishing attacks, and unauthorized access. The main goal of a SOC is to detect, analyze, and respond to security incidents in real time — protecting your data and systems from cyberattacks.
NOC (Network Operations Center), on the other hand, is focused on network performance and availability. It monitors servers, routers, cloud services, and applications to ensure high uptime, smooth operations, and quick resolution of technical issues like outages or slow connectivity.
IT Support or Help Desk deals with end-user problems — things like password resets, software installation, device troubleshooting, or email setup. It’s reactive and user-focused.
To summarize:
🔹 SOC = Protects your systems from cyber threats
🔹 NOC = Keeps your network up, stable, and performing well
🔹 IT Support = Helps employees use technology effectively
Many organizations use a combination of SOC, NOC, and IT support services to achieve full-spectrum IT management and security.
Using secure APIs, agents, or syslog forwarding, a SOC can connect to:
Firewalls (Cisco, Palo Alto, Fortinet)
Endpoint protection (CrowdStrike, Bitdefender, SentinelOne)
Identity systems (Azure AD, Okta)
Email security (Proofpoint, Mimecast)
Cloud platforms (AWS GuardDuty, Microsoft Defender)
Once connected, the SOC aggregates and correlates logs to detect stealthy threats that isolated tools might miss.
You keep your existing investments — while gaining expert oversight, centralized monitoring, and faster response times.
Why Choose Us (Comparison & Pricing)
| Feature Benefit |
In-House SOC |
Outsourced SOC (Generic Vendor) | Traditional Security Providers (Old Model) | Our SOC Services |
|---|---|---|---|---|
| 24/7 Threat Monitoring & Response | Limited staff, fatigue | Available but reactive | Available but costly | Proactive, AI-driven monitoring |
| Skilled Cybersecurity Expertise | Hard to hire & retain | Shared analysts, limited depth | Certified, dedicated experts | Certified threat hunters & analysts |
| Scalability | Requires major infra upgrades | Rigid SLAs/contracts | Very slow, expensive | Flexible, scales instantly with demand |
| Security & Compliance | Gaps in coverage, missed patches | Basic compliance only | Legacy compliance approach | SOC-ready with GDPR, HIPAA, ISO, PCI-DSS |
| Pricing (Monthly Avg.) | 8-12 Lakhs* | 5-7 Lakhs* | 6-9 Lakhs* | 2-4 Lakhs* |
| Hidden Costs | High (infra, tools, staffing) | Add-ons for upgrades | Very high | None, fully transparent |
| Customization | Low flexibility | Standard service bundles | One-size-fits-all | Tailored detection, response & compliance needs |


